In an age where technology permeates every aspect of our lives, home security has not been left behind. There has been an overwhelming growth in the use of wireless alarm systems that are easy to install and flexible.
However, with this rise in wireless technology comes the inevitable question: just how secure are these systems? This article focuses on wireless alarm systems where their advantages and weaknesses are outlined, together with the precautions taken to guarantee their effectiveness as security systems that protect our homes and offices.
Understanding Wireless Alarm Systems
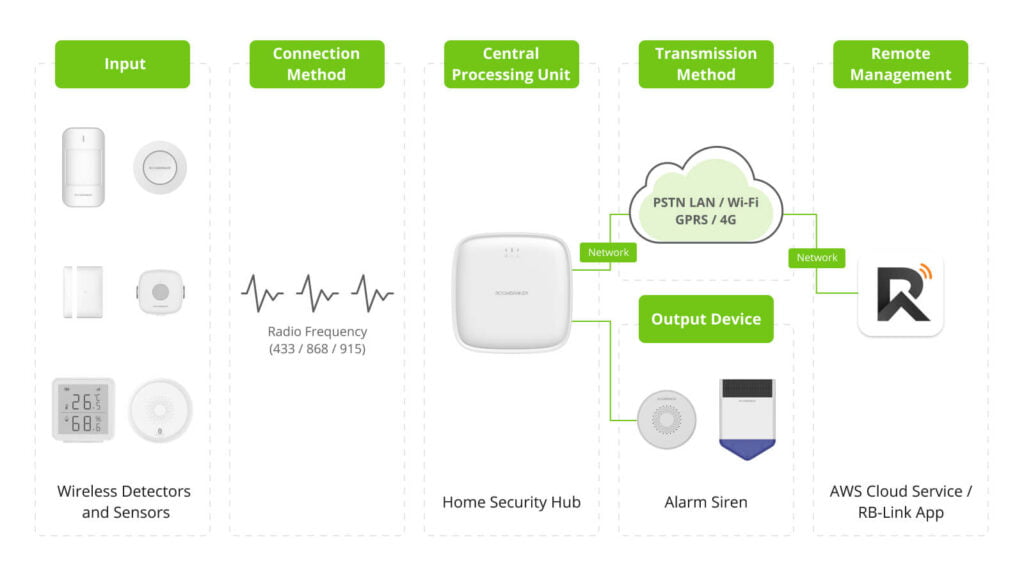
It will be important to first define what a wireless alarm system is and how it works before one can. Wireless alarm mainly has the following primary components: a control panel, various sensors (door and window sensors, motion detectors, glass break detectors), some sorts of cameras, and a communicating module. Unlike the wired systems, these components are connected wirelessly through Radio frequencies (RF) or Wi-Fi eliminating the need for extensive wiring throughout the property.
Key Components:
- Control Panel: The head of the system, receives stimulus from the sensors, and makes a signal for alarm.
- Sensors: Systems, such as alarms, motion sensors, or any other equipment for sensing any other event or change in the environment.
- Cameras: Facilities that should allow for video surveillance or taping of activities can be proposed.
- Communication Module: The device connects the system to the outside monitoring service or the user’s mobile phone.
The Security Advantages of Wireless Alarm Systems
Wireless alarm systems offer several security advantages that contribute to their growing popularity:
No Wires to Cut
One of the most significant advantages of wireless systems is the absence of wires that can be cut by intruders. The wired systems that were developed in the past may be easily defeated since the burglar can easily cut the phone line or even the power leads. Wireless systems exclude this kind of vulnerability, which makes it safer from this kind of interference.
Battery Backup
Many of the wireless alarm components are portable in nature and, therefore, can work during a power blackout. This feature makes sure that your home remains secure at any one time, especially in a situation where the electricity in the neighborhood has been switched off either by a storm or even by an intruder.
Flexible Installation and Scalability
In some cases, it is impossible to install wired systems and that is why wireless systems are also used. The fact that it is flexible makes it possible to install the sensors and cameras at strategic places hence making the security stronger.
Remote Access and Control
Most of the current wireless alarm systems come with smartphone applications that enable the user to control their security system remotely. This type of access is often distant, which is an added control and awareness of the situation to act promptly to a possible security threat.
Compatibility with Smart Home System
Wireless alarm systems co-ordinate with other smart home products creating a single home security network. This can be in the form of smart locks and lights, and added security, as well as convenience, is achieved through the use of voice assistants.
Also read: Are wireless burglar alarms any good?
Potential Vulnerabilities of Wireless Alarm Systems
Despite the numerous security advantages that come with wireless alarm systems, there is so much that can go wrong. Understanding these weaknesses is crucial for both manufacturers and users to ensure the highest level of security:
- Signal Jamming: Sophisticated intruders might use jamming devices to block the radio frequencies used by the alarm system, potentially creating a window of opportunity for a break-in without triggering the alarm.
- Hacking and Cyber Attacks: As with any connected device, wireless alarm systems can be vulnerable to hacking attempts. Cybercriminals might try to exploit vulnerabilities in the system’s software or intercept wireless communications.
- Battery Failure: If batteries are not regularly checked and replaced, critical components of the system could become non-operational, compromising the system’s effectiveness.
- False Alarms: Wireless systems can be more prone to false alarms than their wired counterparts, particularly if not properly installed or maintained. Frequent false alarms can lead to complacency.
- Limited Range: The effectiveness of a wireless alarm system can be compromised if components are placed too far from the control panel or if there are significant obstacles that interfere with signal transmission.
Measures to Enhance Wireless Alarm System Security
Recognizing these potential vulnerabilities, manufacturers and security experts have developed various measures to enhance the security of wireless alarm systems:
Encryption and Frequency Hopping
To decrease the possibilities of signal interception and jammers, most of the existing wireless alarm systems utilize encryption and frequency hopping spread spectrum (FHSS). Encryption is vital since even if one gets an opportunity to intercept a certain signal he/she will not understand what the signal contains. FHSS quickly hops over the range of frequencies that it uses for transmission and thus it is difficult for the jammers to down all the frequencies that are used in the operation of the system.
Regular Software Updates
Mighty manufacturers including Roombanker for instance always provide firmware and/or software enhancements for their wireless alarm systems. These updates may also contain bug fixes including newly found security flaws that put the system at risk, which are then corrected in the update.
Two-Way Communication
There another two types of wireless alarms, the first is the one-way communication between the control panel and sensors, and the second is a two-way one. This enables the system to always check the status and functionality of the components and easily identify instances where some of the components sought to tamper or block the signals.
Backup Communication Channels
It is to address this risk that technological designs typically have multiple forms of communication integrated into the system. For example, a system might be mostly Wi-Fi based however it has cellular or landline backup so that they are guaranteed of their alerts reaching the monitoring station or the user’s smartphone.
Anti-Spoofing Measures
In order to stop hackers from impersonating components of systems that they are trying to intrude into, they put in place anti-spoofing measures. These include, for instance, distinctive numbers for all devices coupled with complicated ways that are hard to penetrate by different and unauthorized devices for communication with the system.

Best Practices for Users
While manufacturers play a crucial role in developing secure wireless alarm systems, users also have a responsibility to ensure their system’s security:
Choose a Reputable Provider
Selecting a well-established, reputable alarm system provider is crucial. Companies with a track record of prioritizing security and regularly updating their systems, such as Roombanker, are more likely to offer robust protection against both current and emerging threats.
Keep Software Updated
Ensure that you check and download updates for the software of the alarm system you are using. Such updates may consist of important security vulnerabilities and additional features that can improve overall security for your property.
Use Strong, Unique Passwords
This goes a long way in ensuring that people cannot break into your wireless alarm system especially if you have an app or website where you monitor the system. It is unwise to include simple information in password creation such as dates of birth, and house addresses, among others it is advisable to use a password generator to create complex passwords which are hard to guess and can store such passwords safely.
Enable Two-Factor Authentication
Quite many of the modern wireless alarm systems have two-factor authentication systems in order to provide a higher level of protection. This is useful as even if a user has his or her password exposed, there will be an added layer of security that needs to be bypassed to access the system.
Regularly Test Your System
Some of the best practices in the use of the wireless alarm system include the following: Perform a test every month to determine whether every part of the system is in good condition. This involves calibrating and checking on the sensors and cameras as well as the communication linkages to check for possible problems before they occur.
Secure Your Home Network
Since some of the wireless alarm systems use wi-fi to operate, it is vital to ensure that your wi-fi has the best encryption like WPA3, and a complex password for the network. This is always the recommendation, but most easily overlooked given how often people rarely update their router’s firmware.
The Future of Wireless Alarm System Security
As technology continues to evolve, so too does the landscape of wireless alarm system security. Several emerging trends and technologies promise to further enhance the security and reliability of these systems:
- AI and Machine Learning: Thanks to AI and machine learning functionalities, threat identification in wireless alarm systems is maintained alongside the likelihood of false alarms. These technologies have the capacity to master the common range of activity in a given home or business, thus they are better placed to identify an intrusion.
- Blockchain Technology: There are some optimistic predictions from specialists in the sphere of security that blockchain can be useful for providing increased reliability and the impossibility of tampering with wireless alarm systems. This way blockchain might add at least another level of system security and a transparent record of all the events and communications within the system.
- Advanced Biometrics: Other types of wireless alarm systems that are commonly used include biometric authentications like Face Recognition and Finger Print Scanning. These technologies provided a higher security measure in arming and disarming the system in comparison to the traditional use of PIN codes.
- 5G Connectivity: 5G technology brings a lot of hope in the improvement of reliability in the operation of wireless alarm systems by allowing faster communication networks to be established. This may lead to advanced security options and also rapid tracking to improve the situational awareness real-time tracking provides.
- Edge Computing: Wireless alarm systems have the potential of low latency by adopting edge computing in their networks. By processing data closer to the source (i.e., within the alarm system itself rather than in the cloud), edge computing can enhance the system’s ability to detect and respond to threats quickly.
Conclusion
Wireless alarm systems have come a long way in their security and reliability. Although they pose some differences when compared to wired systems, the benefits associated with their use as a result of flexibility, convenience, and relatively enhanced capabilities, make them suitable to be adopted by many. The security of these systems depends on a combination of factors: choosing a reputable provider like Roombanker, staying vigilant about system maintenance and updates, and following best practices for user behavior.
New technologies keep on emerging and so the wireless alarm systems security. That is why it is expected that its integration with AI, blockchain, advanced biometrics, and others reflects contemporary exposures and adds an additional level of security. All these developments make it possible for wireless alarm systems to continue being an effective and safe way of protecting our homes and businesses in the ever-advancing technologically-infused world.
